We all know to secure personal information like personally identifiable information (PII), protected healthcare information (PHI) or financial data (e.g. credit card numbers). Companies with intellectual property also understand the importance making sure that proprietary information doesn’t fall into the wrong hands. But what about Board docs and other executive materials that are collaborated on regularly? Sure, companies know not to share them with the outside world, but what about protecting them from insiders?
Who poses the biggest risk?
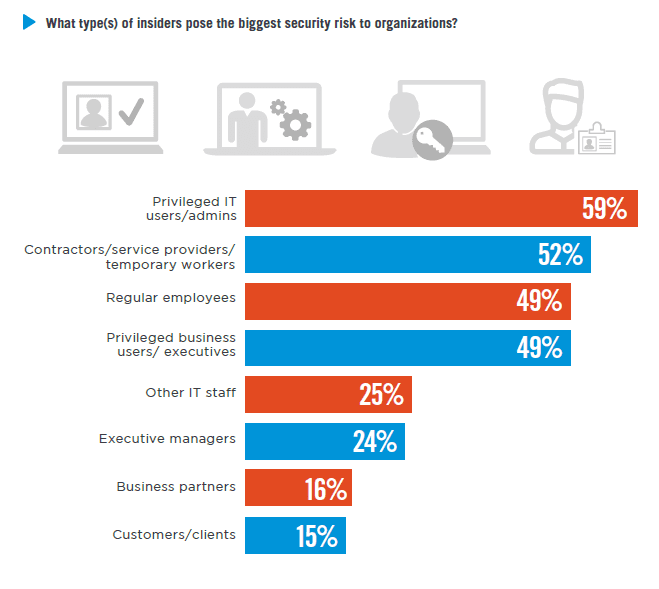
A new Cybersecurity Insiders report on Insider Threats revealed that 49% of companies surveyed feel their privileged business users/ executives pose the biggest cybersecurity risk. Couple that with the 26% concerned about the risk that specifically the Board of Directors and executive management team pose to their organization.
Copyright 2019 – Insider Threat Report
Why? Board members and executives handle the most sensitive and confidential information within a company: financials, mergers and acquisitions, sales numbers, company roadmaps, HR information, etc. Information that is meant for their eyes only and could be damaging to the company and its reputation if leaked or misused. Despite the sensitivity of information handled by privileged business users like Boards and top Execs, in the survey, company data came in fourth (49%) as the data most vulnerable to insider attacks, topped by customer data (63%), intellectual property (55%) and financial data (52%).
This begs the question, do businesses fully understand the data-security risks associated with insider threats?
Understanding internal threats
According to the 2019 Insider Threat Report companies are in fact worried about inadvertent insider breaches such as simple human error (70%), negligent data breaches i.e. knowing the rules but circumventing them without malicious intent (66%), as well as malicious insider breaches for personal gain (62%). However, according to the report “because insiders often have elevated access privileges to sensitive data and applications, it becomes increasingly difficult to detect malicious insider activity (59%). Combined with the proliferation of data sharing apps (49%) and more data leaving the traditional network perimeter (47%), the conditions for successful insider attacks are becoming more difficult to control.”
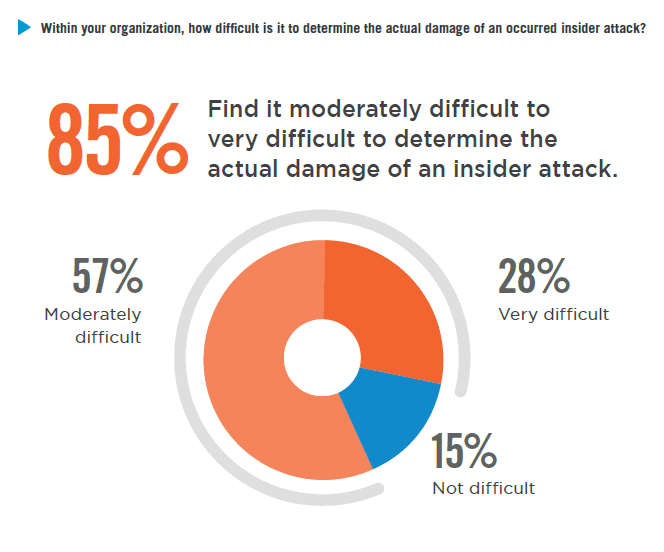
To make matters worse, 85% of organizations surveyed find it moderately to very difficult to determine the actual damage of an insider attack. Many organizations are becoming increasingly aware of insider threat risk and are proactively looking to get ahead of it. For example, an organization we recently worked with came to us because they were concerned about to the confidentiality of their board documents. They needed a data security solution that not only ensures that only approved board members can access these materials, but also keeps administrators from being able to read them.
Copyright 2019 Insider Threat Report
The truth is administrators tend to be extremely overprivileged. They typically have access to all documents stored in collaboration systems, even though they may not have been explicitly granted permissions to access them. That’s because enterprise platforms, like SharePoint, Office 365 and Exchange, give administrators almost unfettered access to an organization’s data. However, while administrators need to be able to manage data, they should not be able to freely access the contents of it. To further complicate the risks involved, if a hacker steals an administrator’s super credentials – the virtual keys to the kingdom – it gives them free reign over the entirety of an enterprise’s information and systems.
Don’t collaboration systems have security in place?
Collaboration solutions themselves are not completely failing to protect data, they are just not adequately meeting the requirements for fully protecting sensitive content. Just as companies have moved to strengthen identity and access security with multi-factor authentication instead of just usernames and passwords, the same approach must be taken for securing sensitive content.
Data-centric security offers a solution to over-privileged user access, as well as ensuring Board and Executive docs can be collaborated on by authorized parties while remaining secure from prying eyes. This is why the NC Protect platform utilizes data-centric security that is both content and context aware to automatically find, classify and secure sensitive data. It is a much better fit for sensitive data that is in an almost constant state of motion across multiple collaboration scenarios. NC Protect dynamically adapts access and security rules to the changing risk profile associated with data as users access and collaborate across multiple locations, organizational boundaries and devices.
NC Protect also restricts an administrator’s ability to look at document contents without impacting their ability to manage it from an IT perspective while still ensuring that authorized users can share and use files according to an organization’s regulations and policies across all devices and locations to reduce the risk of corporate espionage and data theft from insiders, as well as inadvertent sharing mistakes.
Two keys to securing privileged business user collaboration
Collaboration is essential to modern business and Board members and execs need to be able to share highly sensitive document using standard collaboration tools. The key is to one, utilize data-centric technology that makes it easy to do so securely while taking the onus off the users to ensure security isn’t bypassed for ease of collaboration. And, two, ensure that sensitive information can only be accessed by authorized individuals regardless of their system privileges. To collaborate on board and important company information without these security measures in place puts the company’s bottom-line at risk.



