Infographic
Managing Data Security and Governance in Microsoft 365 and SharePoint Server
How to Effectively Manage Data Security and Governance
Data governance and security are about more than just having a strategy in place. You also need the ability to manage risk by identifying issues and potential violations, controlling access to content based on its sensitivity and have auditing capabilities. And most importantly, it needs to be a repeatable process that can be easily adjusted as needed.
This step-by-step illustrated guide lays out each phase; from defining your strategy to using NC Protect to enforce compliance and apply dynamic access and data controls to Microsoft 365, SharePoint Server and file share content. It also provides tips for a successful data security and governance program across your Microsoft stack.
How Does it Work?
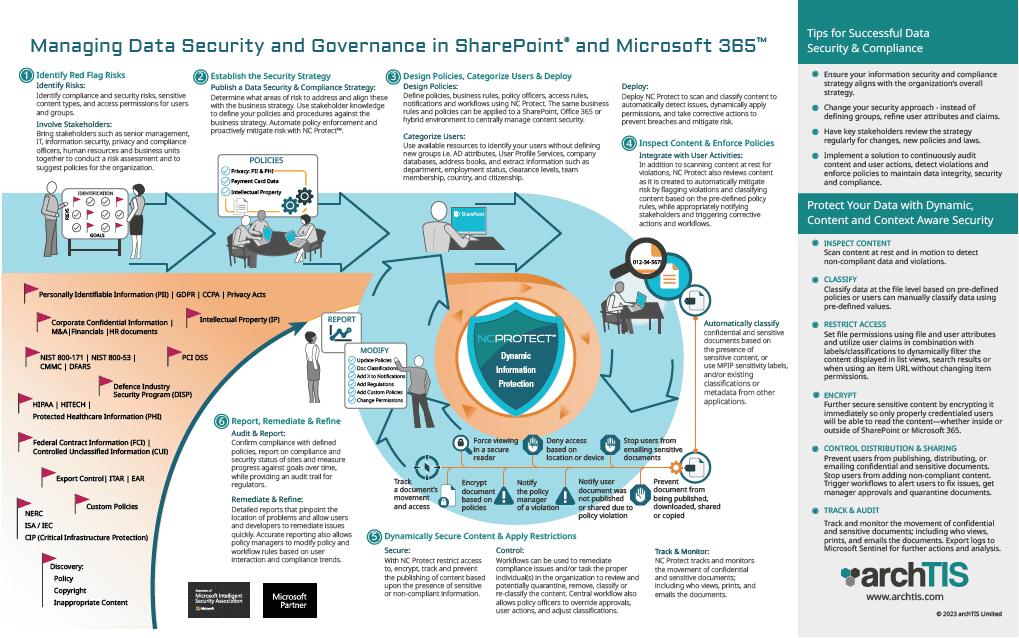
Protect M365 & SharePoint Data with Dynamic, Contextual Security
Inspect Content
Locate all sensitive and confidential data (PII, IP, Board, Contracts, HR, Customer data, etc.) in both on-premises and cloud environments including Microsoft 365, SharePoint Server and file shares.
Regularly scan content at rest and in motion to detect non-compliant data and reclassify changed data.
Classify & Restrict Access
Classify data at the file level based on pre-defined policies or users can manually classify data using pre-defined values.
Set access and protection polices using labels/classifications in combination with user attributes to dynamically filter authorized content without changing item permissions.
Encrypt
Further secure sensitive content by encrypting it when needed so only properly credentialed users will be able to read the content—whether inside or outside of SharePoint or M365.
Use MPIP or RMS encryption, use NC Encrypt dynamically created keys (add on module) or supply and manage your own keys with BYOK support .
Control Distribution
Prevent users from publishing, distributing, or emailing confidential and sensitive documents. Stop users from adding non-compliant content.
Trigger workflows to alert users to fix issues, get manager approvals and quarantine documents.
Track & Audit
Track and monitor the movement of confidential and sensitive documents; including who views, prints, and emails the documents.
Export logs to Microsoft Sentinel or Splunk for further analysis and upstream actions.
