Identifying the Top Insider Threats to Data Security
Last week we unveiled one of the characters in our new Infographic, The Anonymous Admin. This week we look at 2 other insiders from the Infographic found in every organization who are inadvertently (and some deliberately) putting your organization at risk bypassing governance and training, misusing privileges, stealing IP, sharing confidential data with unauthorized parties, and making innocent mistakes. Do you recognize any of them? Don’t despair, we also look at how data-centric security can help stop malicious and careless insiders in their tracks.
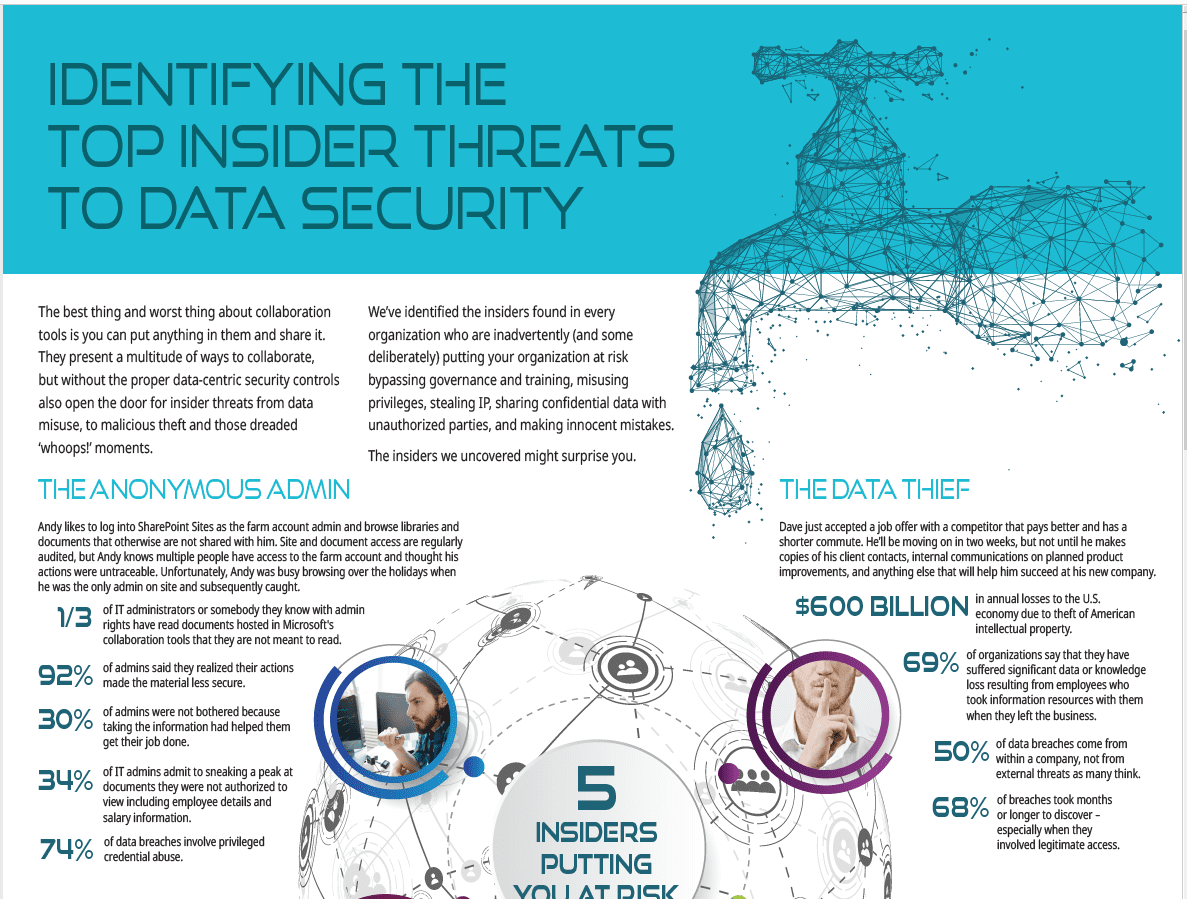
The Data Thief
Dave just accepted a job offer with a competitor that pays better and has a shorter commute. He’ll be moving on in two weeks, but not until he makes copies of his client contacts, internal communications on planned product improvements, and anything else that will help him succeed at his new company.
- $600 Billion in annual losses to the U.S. economy due to theft of American intellectual property.
- 69% of organizations say that they have suffered significant data or knowledge loss resulting from employees who took information resources with them when they left the business.
- 50% of data breaches come from within a company, not from external threats as many think.
- 68% of breaches took months or longer to discover – especially when they involved legitimate access.
The Folder Fiend
Fran creates sub-folder after sub-folder within her document libraries. She sometimes buries them 6, 8 or even 10 layers deep, creating unique permissions which make them hard for others to find and collaborate. She even uploads files to folders on Dropbox to share them with others instead of going through the hassle of asking IT to adjust sharing permissions or provision a new third party user.
- 71% of enterprises struggle to manage and protect unstructured data.
- 4 of 5 organizations don’t know where their sensitive data is located, nor how to secure it.
- 77% of all businesses experience rogue clouds;
- 40% saw confidential data exposed there.
Inside Out Security Is Essential
The truth is insiders pose as much risk as outside threats. Many of today’s security solutions are focused on stopping and detecting outside threats like hackers, malware and ransomware. There are also solutions that look for anomalies in behavior which is great if there’s a malicious insider engaging in repeatable patterns. What about the one’s off data theft like Dave? And employees like Fran who are not trying to be malicious they’re just looking for the fastest and easiest way to get the job done?
Data-centric security has become increasingly important for protecting the enterprise from insider behaviors that put the organization at risk. Securing the perimeter and the application is no longer enough – you need security on the content itself.
A data-centric approach looks beyond the information at rest scenarios in the collaboration tools and associated repositories that traditional access controls and permissions provide. When you consider the data itself, rather than the container it resides in, you need to look at the following factors:
- How it will be created
- How its content will change; and
- How frequently
- How it will be used
- How it will be shared and with whom
When you look at these 5 factors across a document’s lifetime you quickly realize that security and protection must be extended to more than just the collaboration repository. The data-centric approach goes beyond the initial access to information. It considers what you want a user to be able to do once they have access.
Discover How Data-Centric Security Protects Against Other Insider Threats
Meet the 3 other insiders putting your organization at risk and 4 ways a data centric approach can protect against insider breaches.
Get the Infographic